
Introduction: The Security Illusion
Imagine a master thief who doesn’t break your door down but instead, perfectly mimics your voice, walks in with the morning staff, and uses your own keys to open the vault. No forced entry, no fingerprints, no tools left behind. For most traditional security systems, this thief is a ghost.
This is the reality of fileless malware. In an era where we’ve invested billions in fortifying our digital perimeters, this threat emerges from within, exploiting the very trust we place in our systems. The objective of this article is to move the conversation about fileless attacks from the technical shadows into the boardroom, framing it not as an IT problem, but as a fundamental business risk that requires a strategic, organizational response. We will demystify how it works, highlight its unique dangers, and provide a clear roadmap for building a resilient defense.
What Are We Trying to Solve? The Awareness Gap
Many cybersecurity strategies are still built for the last war. They focus on keeping bad files out. Fileless malware renders this obsolete. This article aims to solve the critical awareness gap between technical teams, who are often fighting this new threat with one hand tied behind their backs, and business leaders, who may not understand why their significant security investments are failing.
We will shed light on the “how” and “why,” but more importantly, we will connect these technical details to business outcomes: financial loss, reputational damage, and operational paralysis. We will also explore the convergence of fileless techniques with AI-powered attacks, presenting a new challenge that demands our immediate attention.
A Short Story from the Real World: The Heist Without a Trace
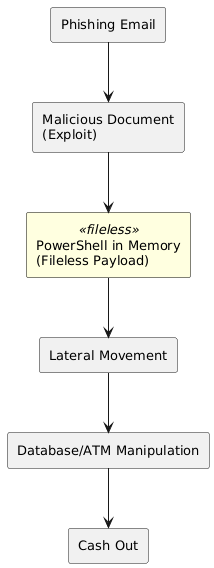
In 2017, a sophisticated criminal group targeted dozens of banks worldwide. Their weapon? The Carbanak gang. In one classic attack, they started with a simple phishing email to a bank employee. The email contained a malicious document.
When opened, the document didn’t download a suspicious .exe file. Instead, it exploited a vulnerability in Microsoft Office to run a PowerShell script directly in the computer’s memory. This script gave the attackers a foothold. They lurked, moved laterally through the network for months, and learned the bank’s processes. Finally, they struck not by directly stealing money, but by manipulating the database and ATMs, instructing them to dispense cash at specific times to mules on the ground.
The total take was over $1 billion. In many cases, because the attack was almost entirely fileless, incident responders found virtually no malware to analyze. The attackers were in and out like ghosts, using the bank’s own administrative tools as their burglary kit.
Demystifying the Ghost: What is a Fileless Virus?
At its core, a fileless virus—more accurately called fileless malware or a “Living-off-the-Land” binary—is a type of malicious activity that avoids writing files to disk. Instead of relying on a malicious executable that can be scanned and quarantined, it operates directly within a system’s volatile Random Access Memory (RAM), leveraging legitimate, trusted system tools to carry out its objectives.
Think of it this way:
- Traditional Malware: A burglar who brings their own crowbar (malicious file) to break in.
- Fileless Malware: A burglar who convinces the janitor (a trusted system tool) to open the door and then uses the family’s own tools inside the house (system commands) to crack the safe.
The term “fileless” can be slightly misleading, as some techniques may involve writing small, benign-looking scripts or using registry entries. The key differentiator is that the primary malicious payload never touches the disk; it lives and dies in memory.
The Anatomy of an Illusion: How Fileless Malware Works
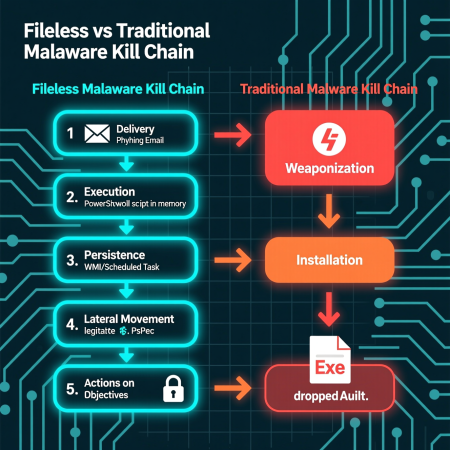
Understanding the “how” is crucial for developing effective countermeasures. A fileless attack follows a distinct lifecycle, often referred to as the Cyber Kill Chain.
- Delivery: The attacker needs an entry point. This is typically achieved through:
- Phishing Emails: With malicious links or attachments (like the Carbanak case).
- Compromised Websites: Using exploit kits that target browser vulnerabilities.
- Stolen Credentials: Using valid login details to access systems directly.
- Execution & Exploitation: This is where the magic happens. The initial vector (e.g., a document macro) doesn’t drop a file. It executes a command that leverages a trusted system tool. The most common accomplices are:
- PowerShell: A sysadmin’s best friend, an attacker’s dream. It can download, decode, and execute payloads directly from memory.
- Windows Management Instrumentation (WMI): Used for remote system management, it can be abused to execute commands, persist, and gather intelligence.
- Regsvr32 / Mshta: Legitimate Windows utilities that can be tricked into loading and executing malicious scripts from remote servers.
- Persistence: Since memory is cleared on reboot, the attacker needs a way to stay. They achieve this by planting a “trigger” that re-triggers the infection. This could be a scheduled task, a WMI event subscription, or a registry modification that runs a script to pull the payload back into memory.
- Lateral Movement & Data Exfiltration: Once inside, the attacker uses the same trusted tools (like
net.exeorpsexec) to explore the network, locate valuable data, and exfiltrate it—often by hiding it in normal network traffic.
Why Should You Care? The Business Impact of an Invisible Threat
If you’re a C-level or business manager, you might ask: “Why is this my problem?” The answer lies in the profound business implications.
- Evasion of Security Investments: Fileless attacks make a mockery of traditional, signature-based antivirus and firewalls. Your multi-million dollar security stack may be blind to this threat, representing a direct failure of ROI and a waste of resources if not complemented with modern tools.
- Extended Dwell Time: Because they are so hard to detect, fileless attackers can live inside a network for months (the “mean time to detect” is often over 200 days). During this time, they are stealing your most sensitive intellectual property, financial data, and customer information.
- Increased Cost of a Breach: A longer dwell time and a more sophisticated attack lead to a vastly more expensive cleanup. The costs associated with investigation, remediation, legal fees, regulatory fines, and reputational repair are astronomical.
- Operational Disruption: The ultimate goal may not be theft. It could be ransomware deployed via fileless methods, bringing your entire operation to a halt. Or it could be sabotage, silently manipulating data or disrupting critical infrastructure.
This isn’t just a technical nuisance; it’s a direct threat to your company’s viability.
The Great Divide: Fileless vs. File-Based Malware
Let’s make the distinction crystal clear. This isn’t just an evolution; it’s a paradigm shift.
| Characteristic | File-Based Malware | Fileless Malware |
|---|---|---|
| Primary Residence | Hard Disk Drive (HDD/SSD) | Random Access Memory (RAM) |
| Detection | Relatively easy with signatures & heuristics | Extremely difficult for traditional AV |
| Footprint | Leaves a physical file artifact | Leaves minimal-to-no disk footprint |
| Tools Used | Brings its own malicious executables | Uses legitimate system tools (LoLBins) |
| Persistence | Modifies system files or startup folders | Uses native mechanisms (WMI, Tasks, Registry) |
| Analogy | An armed invader | A ghost possessing a staff member |
A Brief History: What Was the First Fileless Virus?
While the term “fileless” is modern, the concept is not. The Code Red worm in 2001 is often cited as an early example. It exploited a vulnerability in Microsoft’s IIS web server software. Upon infection, it existed entirely in the web server’s memory, defacing websites and launching attacks on other servers. It never wrote itself to the disk, making it difficult to eradicate without a reboot. This early example proves that the underlying techniques have been a threat for decades, but they have now become the mainstream for sophisticated attackers.
The Modern Attack Vectors: How Fileless Malware is Spread
The initial infection vector is often the weakest link in the chain: the human element or unpatched software.
- Phishing & Spear-Phishing: The #1 delivery method. A convincingly crafted email that tricks a user into enabling macros or clicking a link that triggers the exploit.
- Drive-by Downloads: A user visits a compromised, legitimate website that hosts an exploit kit. The kit silently probes the browser for vulnerabilities and, if found, executes the fileless payload without any user interaction.
- Stolen Credentials & Remote Access: Attackers use credentials bought on the dark web or obtained through other breaches to log into systems (like RDP, VPN) directly and manually execute fileless commands.
- Supply Chain Attacks: Compromising a trusted software vendor or a third-party library can introduce a fileless backdoor into your environment through a “trusted” update.
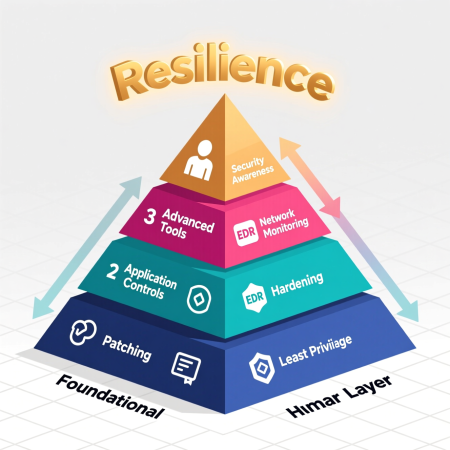
Building the Digital Immune System: How to Defend Against Fileless Attacks
You cannot fight a ghost with a club. Defending against fileless malware requires a strategic shift from a “prevention-only” mindset to a “Assume Breach” posture. Here is a multi-layered defense framework:
- Endpoint Detection and Response (EDR) is Non-Negotiable: This is the cornerstone. EDR tools continuously monitor endpoints for suspicious behavior, not just bad files. They can detect the sequence of
winword.exespawningpowershell.exe, which then makes a network connection to a known-bad IP. This behavioral analysis is key to uncovering fileless attacks. - Strict Application Control and Privilege Management:
- Principle of Least Privilege: No user should run with administrative rights by default. Most fileless techniques require high privileges. This single step can stop many attacks dead in their tracks.
- Application Whitelisting: Use tools like AppLocker to dictate which programs are allowed to run. If your accounting department doesn’t need
regsvr32.exe, block it.
- System Hardening and Logging:
- Disable or Constrain powerful scripting tools like PowerShell where they are not needed. Where they are needed, enable Constrained Language Mode and deep logging to record every command executed.
- Patch Relentlessly: While fileless attacks don’t always rely on exploits, they often do for initial entry. Patching removes these entry points.
- Network Segmentation and Monitoring: If an attacker gets in, don’t make it easy for them to go everywhere. Segment your network to limit lateral movement. Use network traffic analysis to spot anomalous data flows, even if they originate from “trusted” systems.
- Security Awareness Training: Continually train your staff to recognize phishing attempts. They are the human firewall that can block the initial delivery vector.
The New Frontier: AI and the Future of Fileless Threats
The game is about to change again. Artificial Intelligence is poised to supercharge fileless malware.
- AI-Powered Adaptation: Imagine a fileless payload that uses AI to learn the normal “sound” of your network. If it detects a security analyst investigating its activities, it could automatically switch tools or go dormant, evading EDR rules based on static behavior.
- AI-Generated Social Engineering: Phishing emails, the primary entry point, will become hyper-personalized and virtually indistinguishable from legitimate communication, making the initial compromise far more likely.
- Automated Attack Chains: AI could autonomously chain together multiple living-off-the-land techniques, constantly evolving its attack path in real-time to find the weakest link in your defenses.
The defense against this will equally rely on AI-driven security systems that can analyze behavior at scale and predict malicious intent before the attack fully unfolds.
Conclusion: From Fear to Resilience
The threat of fileless malware can seem daunting. It’s invisible, sophisticated, and bypasses our traditional defenses. However, it is not undefeatable. By understanding its nature and shifting our strategy, we can build a more resilient organization.
This is not just a task for the IT department. It requires C-level buy-in for investing in modern tools like EDR, enforcing strict security policies like least privilege, and fostering a culture of security awareness from the boardroom to the breakroom. The goal is to build a digital immune system that can identify and isolate threats based on their behavior, regardless of whether they ever leave a file behind.
The era of the invisible adversary is here. Will you be ready?
TLDR; Fileless malware is a dominant, high-risk threat that uses your system’s tools against you, evading traditional security. Defense requires a strategic shift: invest in behavioral monitoring (EDR), enforce least privilege and application control, patch diligently, and train your users. For business leaders, this is a critical operational risk, not just an IT issue.
Don’t let the unseen adversary become your biggest crisis. Begin your journey to resilience today.
- For Specialists/Managers: Propose a pilot for an EDR solution and conduct a threat-hunting exercise focused on PowerShell and WMI activity.
- For C-Level & Business Leaders: Request a briefing from your CISO on your organization’s specific preparedness for fileless attacks. Ask pointed questions about EDR coverage, privilege management, and incident response plans for behavioral threats.
The time to act is now, before the ghost is already in the machine.